Sniffing (also called as packet sniffing) refers to the use of a device or program to capture vital information from a wired or wireless network traffic using data interception technology. The objective of sniffing is to steal various information such as passwords of applications like email and FTP, contents in the email, chat conversations, files that are in transfer from one system to another and so on.
Protocols that send and receive data in a raw format without encryption are easily susceptible to sniffing attack. Here is a list of some of the common protocols that are vulnerable to sniffing:
· Telnet:
Keystrokes including usernames and passwords.
· HTTP:
Data sent in clear text.
· SMTP:
Passwords and data sent in clear text.
· FTP:
Passwords and data sent in clear text.
· POP:
Passwords and data sent in clear text.
TYPES OF SNIFFING
Sniffing is mainly classified into two types as follows:
Passive Sniffing
Passive sniffing is fairly simple which involves just connecting to the target network and waiting for the packets to arrive at your host for sniffing. This type of sniffing works only in an unswitched network environment where the individual hosts are interconnected using a hub.
In a hub type of network environment, traffic (packets) from all hosts are sent to all ports on the network. This makes it possible for the hacker’s computer to secretly intercept and sniff packets that belong to other computers on the same network.
In order to carry out passive sniffing, the hacker will simply hook up his laptop to the network and runs a sniffing software to silently capture the packets that arrive at his port.
Since passive sniffing works by simply exploiting the existing vulnerability of unswitched networks without making additional modifications, it is often hard to detect.
Active Sniffing
Active sniffing is the one that is often performed on a switched network environment. Here individual hosts on the network are interconnected using switches that keeps record of MAC addresses (hardware addresses) of all hosts connected to it. With this information the switch can identify which system is sitting on which port so that when the packets are received they are intelligently filtered and forwarded only to the intended ports.
This makes the packet sniffing very difficult on switched network as the traffic from all hosts does not flow to all ports on the network. However, it is still possible to actively sniff packets on switched networks using techniques such as ARP poisoning and MAC flooding which are discussed below.
TECHNIQUES FOR ACTIVE SNIFFING
Since most computer networks today uses switches instead of hubs, active sniffing proves more feasible under practical conditions. The following are some of the important techniques used in active sniffing:
ARP Poisoning
Before actually going into ARP poisoning, let us first try to understand what ARP actually means.
What is an ARP?
ARP which stands for Address Resolution Protocol is responsible for converting IP address to a physical address called MAC address in a network. Each host on a network has a MAC address associated with it which is embedded in its hardware component such as NIC (Network Interface Controller). This MAC address is used to physically identify a host on the network and forward packets to it.
When one host wants to send data to another, it broadcasts an ARP message to an IP address requesting for its corresponding physical address. The host with the IP address in the request replies with its physical address after which the data is forwarded to it. This ARP request is cached immediately and stored in an ARP table to ease further lookups. So, ARP poisoning (also known as ARP spoofing) is where the hacker goes and pollutes the entries in the ARP table to perform data interception between two machines in the network. For this, whenever a source host sends an ARP message requesting for the MAC address of target host, the hacker broadcasts the MAC address of his machine so that all the packets are routed to him and not the target host that is intended to receive. The following figure shows an illustration of how ARP poisoning is performed.
 |
| ARP poisoning |
Tools for APR Poisoning
The following are some of the tools that can be used to carry out ARP poisoning:
1. Ettercap
This is an open-source network security tool used for performing sniffing and man-in-themiddle attacks on a local network. It is capable of intercepting network traffic and capturing vital information like passwords and emails. It works by putting the network interface device into promiscuous mode and poisoning ARP entries of the target machines to sniff traffic even on switched network environment. It can be downloaded from the link below:
Download Ettercap: http://ettercap.github.io/ettercap/
2. Nightawk
This is a simple tool for performing ARP spoofing and password sniffing. It has the ability to capture passwords from web login forms implemented on protocols like HTTP, FTP, SMTP and POP. It can be downloaded from the link below:
Download Nightawk: https://code.google.com/p/nighthawk/
MAC Flooding
MAC flooding is another type of sniffing technique used in a switched network environment that basically involves flooding the switch with numerous unnecessary requests. Since switches have limited memory and processing capabilities to map MAC addresses to physical ports, they gets confused and hits their limitation.
When switches hits their limitation they will fall into an open state and starts acting just like a hub. That means, all traffic gets forwarded to all ports just like in case of an unswitched network so that the attacker can easily sniff the required information.
Tools for MAC Flooding
EtherFlood is an easy to use open-source tool to carryout MAC flooding in a switched network environment. The download link EtherFlood is mentioned below:
Download EtherFlood: http://ntsecurity.nu/toolbox/etherflood/
DNS CACHE POISONING
DNS cache poisoning (also known as DNS spoofing) is a technique similar to ARP poisoning where the Domain Name System (DNS) resolver’s cache is polluted by introducing manipulated data into it. So, whenever users try to access websites, the poisoned DNS server returns an incorrect IP address thereby directing the users to the attacker’s computers.
The DNS is responsible for mapping the human readable domain names to their corresponding addresses. In order to improve the speed of resolution, DNS servers often cache the previously obtained query results. Before caching or forwarding the query results, the DNS server has to validate the response obtained from other servers to make sure that it has come from an authoritative source. However, some servers are configured with less security features where they fail to properly validate the source of response. Hackers can exploit this vulnerability to introduce malicious records to the DNS cache so as to redirect a large group of Internet users to their computers. When a DNS cache is said to be poisoned, it will affect all those Internet users who have configured their systems to use it as their DNS server. The following figure illustrates the working of DNS cache poisoning attack.
 |
| DNS Cache Poisoning |
As shown in the above figure, a user will place a request to the DNS server for resolving “facebook.com”. Since the DNS server does not have the IP in its cache, it forwards the same request to the next DNS server. Now, a rouge DNS server picks up the request and replies with a fake IP for the query “facebook.com”. Without actually validating the response, the DNS server forwards the result to the user and also stores the result in its cache. As a result the cache gets poisoned.
The user is now directed towards the fake “Facebook” server maintained by the hacker instead of the real one. All the subsequent requests from other users for “facebook.com” is also answered by the compromised DNS server using its poisoned cache data.
In this way it is possible for the hacker to victimize a large group of people and hijack their personal information such as passwords, emails, bank logins and other valuable data.
MAN-IN-THE-MIDDLE ATTACK
Man-in-the-middle is referred to a kind of attack where the attacker intercepts an ongoing communication between two hosts in a network with an ability to sniff the data or manipulate the packets exchanged between two communicating parties. This attack is somewhat similar to the one shown in the below figure from the previous section.
Another good example of man-in-the-middle attack is an active eavesdropping carried out by the attacker by making two independent connections with the victims to make them believe that they are chatting with each other. But the entire conversation is actually controlled by the attacker as illustrated in the following figure
 |
| Man In The Middle Attack |
TOOLS FOR SNIFFING
After going far enough into the theoretical concepts of sniffing, let us now look at some of the popular sniffing tools and learn how to use them to carry out various kinds of attacks.
WireShark
Wireshark is free and open-source packet analyzer program used for network troubleshooting and analysis. It is available for both Windows and Linux operating systems and can be downloaded from the following link:
Download WireShark: https://www.wireshark.org/download.html
Once you have installed WireShark on your Windows computer, start the program by running it with administrator privileges.
 |
| WureShark |
From the menu options, click on “Capture” and select “Options” from the drop down menu. This will show a list of available interface devices for sniffing.
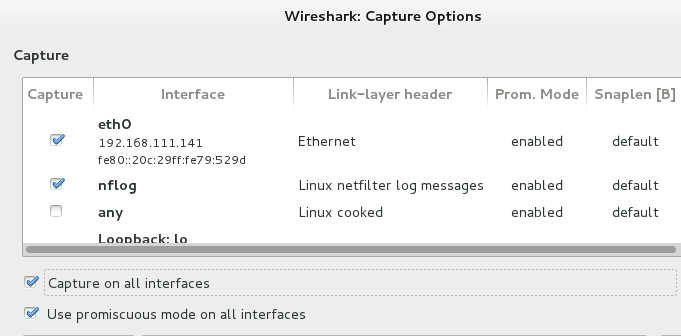 |
| Available Interface device |
You can either select a particular device or choose to capture on all interfaces. Also make sure that “promiscuous mode” is activated. When you are done click on the “Start” button to begin the sniffing process.
This will start capturing all the incoming and outgoing traffic on the network as shown in the following figure below:
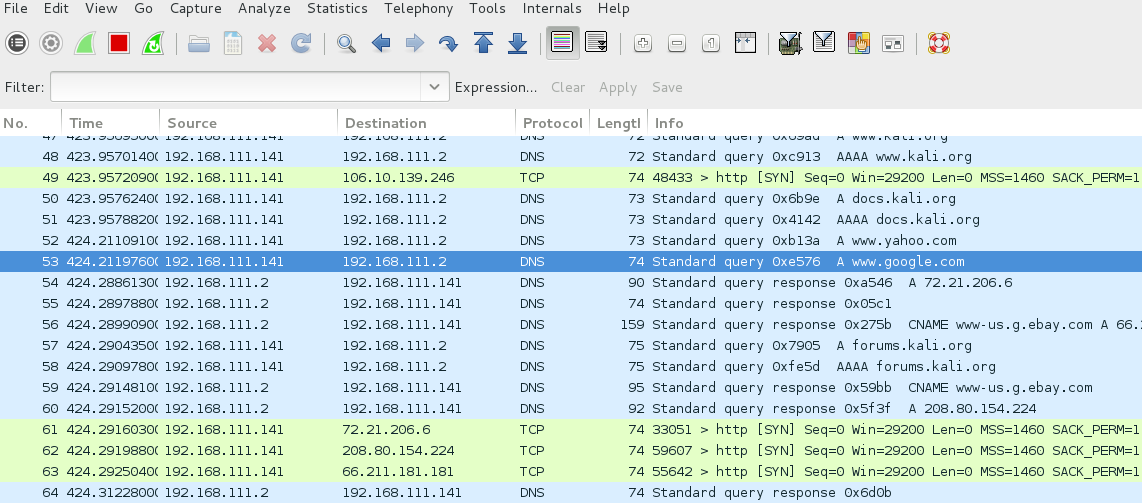 |
| Packet Capturing |
Run this tool for as long as you want and when you feel that you are done with capturing enough data, stop the sniffing process by pressing the “Stop” button displayed in red colour at the top.
In order to analyze the captured data, you will have to set filters in for filtering the type of data that you are looking for. For example, if one is looking to capture passwords from login forms which are normally sent using the HTTP POST request method, you can set the filter as http.request.method == “POST”. This will help you narrow your results and find what you are looking for.
Once the filter is set, right-click on the desired result that you want to analyze and select “Follow TCP Stream”. This will open up the entire TCP stream in a new window. Here you can carefully analyze the data to find out the password entered by users in unencrypted login forms as shown in the sample snapshot below.
 |
| TCP Stream |
Cain & Abel
This is another powerful network sniffer which has many other built-in features such as password cracking, ARP poisoning and MAC spoofing. It proves as an all-in-one tool for performing various attacks such as sniffing, man-in-the-middle attack and ARP cache poisoning.
 |
| Cain and Abel |
You can download this tool from the following link:
Download Cain & Abel: http://www.oxid.it/cain.html
SMAC
SMAC is a handy tool that allows you to spoof the MAC address on your machine. Using this tool it is possible to set the MAC address of your choice so as to easily fool other machines on the network to send their information to your machine.
The following snapshot shows the SMAC tool in action:
 |
| SMAC |
The download link for SMAC is given below:
SMAC Download : http://www.klcconsulting.net/smac/
COUNTERMEASURES
After knowing about various sniffing methods and the tools used to carry out them, it is time to shed some light on possible countermeasures that can be taken to prevent such attacks on your network.
· Restrict
physical access to the network for unintended users. This will stop the
attacker from installing the packet sniffer on the network.
· Use
encryption on the network so that even if the attacker manages to sniff the
packets, he will not be able to see the information in a plain text format.
· Permanently
adding the MAC address of the gateway to the ARP cache will prevent the
attacker from ARP spoofing the gateway.
· In
case of a small network using static IP addresses and static ARP tables will
prevent hackers from adding spoofed ARP entries.
· In
case of a large network install switches that come with port security features
which makes it impossible to spoof.
· Use
tools like Arpwatch or an IDS (Intrusion Detection System) to
monitor and detect sniffing activities on the network.


0 comments:
Post a Comment